Identifying the servers hosting critical applications in your environment is crucial so that alerts for unusual events on those servers are put on higher priority for your security operations team.
One of the approaches we can take to identify the critical assets is by leveraging the load balancer. This could be a head start to build a mini-CMDB (Configuration Management Database) for assets for your sec ops team.
Below is an over-simplified example of network architecture showing a critical web app named “example.com” web app hosted by 5 servers which are load balanced on F5 (VIP : 172.22.23.11). Out of the 5 servers, only 3 servers are active.
In this example, the goal is to get the active servers behind the VIP.
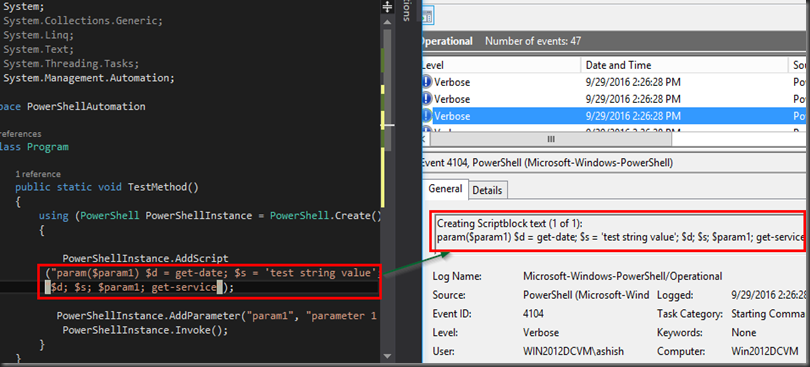
I wrote a PowerShell script to get all the active servers behind all the active VIPs on the a given load balancer.
Why this approach?
- If the server is hosting an app which is critical, It has to be load balanced.
- If a new server is added to an existing VIP, this script will get it.
- If a server is decommissioned, It would be inactive to the load balancer and therefore the script will ignore it.
If the script is scheduled to run periodically, we will have an up-to-date list of servers which are running critical applications. That list can be integrated with SIEM to prioritize alerts from the those servers.
The script
The PowerShell script makes use of PowerShell cmdlet for F5 which can be downloaded from the below location.
https://devcentral.f5.com/d/microsoft-powershell-with-icontrol?download=true
The downloaded file is a .zip file. You copy to your local folder, unzip it and run .\setupSnapin.ps1 which is unzipped file. You may get an error :
Could not load file or assembly iControlSnapin.dll or one of its dependencies. Operation is not supported. (Exception from HRESULT: 0x8013515
Make sure the “Unblock” is checked from all the files in the unzipped file including “setupSnapin.ps1”
.\setupSnapin.ps1 should work fine now.
Below is the script. You will need to change the F5 IP address and the partition name where the virtual servers reside. The output of the script is saved to a file named “ServerList.csv”
Add-PSSnapIn iControlSnapIn
function GetPoolMembers($poolname,$virtual_server_name_only,$virtual_ip)
{
$poolmembers = $ic.LocalLBPool.get_member_v2(@($poolname))
$test = $poolmembers[0]
write-output($poolname)
write-output ('Backend servers and ports :')
$member_status = $ic.LocalLBPool.get_member_object_status($poolname,$poolmembers)
$node_index = 0
foreach($poolmember in $test)
{
$availability_status = $member_status[0][$node_index].availability_status
if($availability_status -eq "AVAILABILITY_STATUS_GREEN")
{
$ip_address = $poolmember[0].address.replace($active_folder,"").replace("/","")
write-output($ip_address )
$global:server_node_details += $ip_address+","+$virtual_server_name_only + "," + $virtual_ip +"`n"
write-output($global:server_node_details)
}
$node_index = $node_index + 1
}
write-output $global:server_node_details
}
$global:server_node_details = "sep=,"+"`n"
$global:server_node_details += "Server IP,F5 Virtual IP,F5 Virtual Server Name" +"`n"
$connection = Initialize-F5.iControl -Hostname <Your F5 IP Address> -Credentials (Get-Credential)
$ic = Get-F5.iControl
# Set the active folder aka partitions where you know the virtul servers exist
$active_folder = "/YourPartitionName/"
$ic.SystemSession.set_active_folder($active_folder)
# get list of all the virtual servers
$virtual_server_list = $ic.LocalLBVirtualServer.get_list()
$virtual_server_with_server_side_profile = @()
foreach($virtualserver in $virtual_server_list)
{
$object_status = $ic.LocalLBVirtualServer.get_object_status($virtualserver).availability_status
if($object_status -eq "AVAILABILITY_STATUS_GREEN")
{
$virtual_server_name_only = $virtualserver.replace($active_folder,"")
write-output ('Virtual server name ' + $virtualserver)
write-output ($object_status)
$addresses = $ic.LocalLBVirtualServer.get_destination_v2($virtualserver)
write-output($addresses.Length)
$virtual_ip = $addresses[0].address.replace($active_folder,"")
write-output('Virtual IP address : ' + $virtual_ip )
$pool_name = $ic.LocalLBVirtualServer.get_default_pool_name($virtualserver)
GetPoolMembers $pool_name $virtual_ip $virtual_server_name_only
}
}
$global:server_node_details | Out-File -FilePath .\ServerList.csv
The output
The script output has 3 columns for each server in with Its Virtual IP and Virtual server name.
Virtual server name is an identifier for the Virtual IP address on the load balancer. That name provides an indication of what that server is used for. This approach groups servers by their Virtual server name and saves identifying each server for what it is used for.
In the below hypothetical example for the output, servers 172.22.1.1, 172.22.1.2 and 172.22.1.3 running example.com web app.